|
Introduction
Safety at business level
Due to digitalization, Cybersecurity for SMEs is a crucial issue today. Cyber-attacks are increasingly targeting small and medium-sized enterprises that are not as protected as large corporations.
Cybersecurity is a set of practices to defend computer systems and software from cybercrime.

Cybercrime is any criminal activity that takes place in the digital world, involving a computer, a networked device or a network, and intended to achieve a certain purpose or benefit, which can be of different kinds. Cybersecurity covers many areas: network security, app security, information security, user security, etc. Let’s see some concepts to consider cybersecurity from a business level, to end up at the end of the course with a basic guide of Cybersecurity.
Ransomware is a type of malicious software that encrypts information on different devices. Using this method, cybercriminals extort money from their victims by demanding a ransom in exchange for regaining access to their data.

Ransomware, is a type of malware that prevents users from accessing their system or personal files and demands the payment of a ransom in order to regain access to them
Malware means malicious software. One of the most common cyber threats, malware is software that a cybercriminal or hacker has created to disrupt or damage a legitimate user’s computer.
Often spread via an unsolicited email attachment or legitimate-looking download, malware may be used by cybercriminals to make money or in politically motivated cyber-attacks. There are a many different types of malware, like Viruses, Trojans, Spyware, Ransomware, Adware, Botnets.

An antivirus is a program that detects malware, blocked them, and eliminate them to prevent infecting the device. There exist different kinds of antivirus, to choose the most suitable one for you or your business, you will have to take in account the specifications of the device to be protected and some criteria to be taken in account.
There is plenty of antivirus software available, so, when it comes to choosing them, consider these criteria:

Which is the difference between antivirus and anti-malware?
They both refer to software designed to detect, protect and remove malicious software. Despite what the name might suggest, antivirus software protects against more than just viruses; it simply uses a slightly old-fashioned name to describe what it does. Anti-malware software is also designed to protect against viruses, and simply uses a more modern name that encompasses all types of malicious software, including viruses.

Knowing this, anti-malware can prevent the occurrence of a viral infection and remove infected files. However, anti-malware is not necessarily equipped to restore files that a virus has changed or replaced.
Security Patches. Vulnerability
It is an important part of cybersecurity in business as it helps to avoid vulnerability gaps in the company's systems, by updating all their equipment and devices. This includes computer applications and operating systems, electronic equipment firmware and anti-malware software.
Patches and updates are created by the actual developers of the software and serve to improve its performance by fixing security bugs and adding new features.
Protecting Business Data: Backup Basics
Quite simply, a data backup is nothing more than a copy of the files on your computer or device. And, as evidenced by the many threats described above, maintaining a backup of your important business files and data is essential for a number of important reasons.
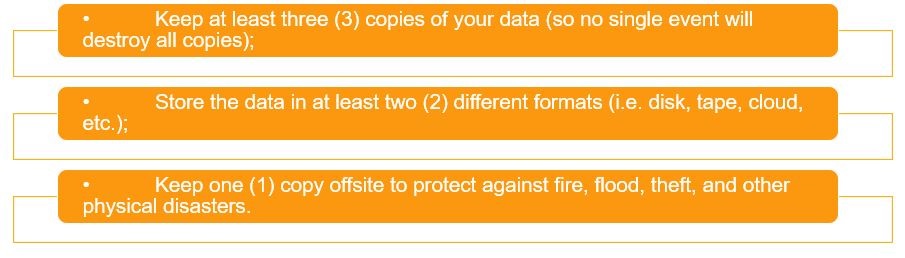
Any backup is better than no backup, however, not all backup devices and technologies are equal or offer the same levels of protection. For optimal protection, it is best to safeguard your data using the 3-2-1 rule, which is as follows:
Protecting Wireless Networks

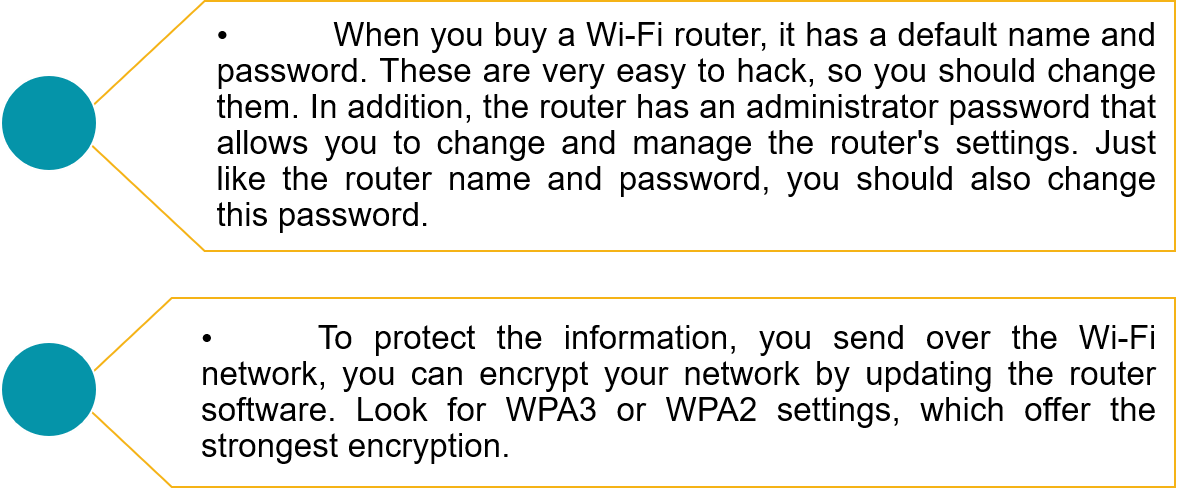
Using a wireless network gives you the convenience of being able to work and use your computer virtually anywhere, and to connect to other computers on the network or access the Internet. However, if your wireless network is not secure, there are significant risks. For example, a hacker could intercept any data you send or receive, access your shared files, hijack your Internet connection and exhaust your bandwidth or download limit.
Employees can make your company vulnerable to attacks, or help prevent them. Numerous studies show that a large amount of data loss comes from internal employees who, in most cases through carelessness or misinformation, give cyber criminals access to their networks.
There are many scenarios that could result in attacks in which the access routes are employees. For example, an employee losing a work tablet, giving away their login credentials, or opening fraudulent emails, which deploy viruses on the network.
To protect against insider threats, it is crucially important to invest in quality cybersecurity training for employees that gives them the tools they need to act in the face of various situations and risks.

Policies. Cybersecurity Policy. What is a cyber security policy?
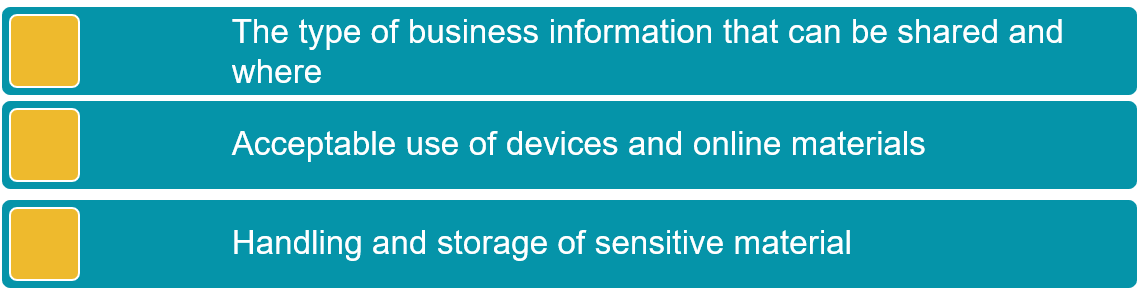
To prevent cybercrime, it is important not only to train your employees in cybercrime prevention, but also to create a company cybersecurity policy. This will help clearly outline the guidelines for transferring company data, accessing private systems, and using company-issued devices. When you prepare your policy, ensure it guides your employees on:
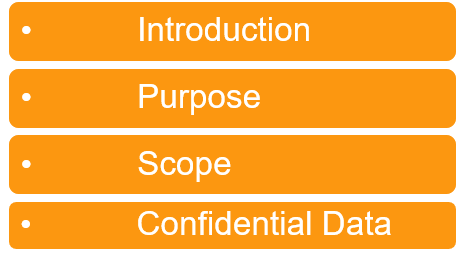
A complete cybersecurity policy template will include basic parts as follows:
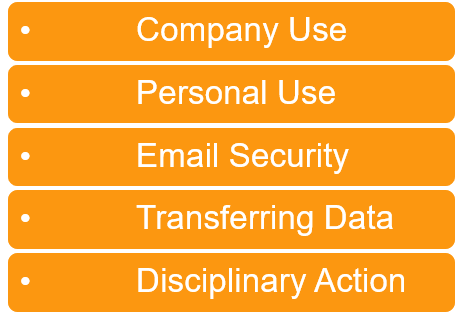
Device Security:

Cybersecurity at user level
End-user training is important because it addresses the most unpredictable cyber security factor - people. If good security practices are not followed, anyone can accidentally introduce a virus into an otherwise secure system. Teaching users to pay attention to risk factors is critical to the security of any organization.

Protect data on your devices
Personal data and sensitive data. Are they the same?
What is personal data?
Personal data is any piece of information that someone can use to identify, with some degree of accuracy, a living person. For example, the e-mail address of an employee of a company is considered personal data, because it indicates that that person works for the company. A physical address or a telephone number is also personal data, because this information can be used to contact the person.
Anything that can affirm your physical presence somewhere is also considered personal data. For example, recordings from security cameras are personal data, as are fingerprints.

Some examples could be:

What is sensitive personal data?
Sensitive personal data is a specific set of “special categories” that holds a stronger law protection, and must be treated with extra security, upon specific approval of the subject which that data refers to. This includes information pertaining to:

Sensitive personal data should be stored separately from other personal data, preferably in a locked drawer or filing cabinet. As with personal data in general, it should only be kept on laptops or handheld devices if the file has been encrypted and/or pseudonymised.

Cybersecurity starts with strong physical security. This includes storing documents securely, locking them in a room or cabinet, limiting the physical access to sensitive data, deleting information correctly and shredding sensitive data documents when they are no longer needed. Allow access to personal and financial information just to the staff who really need it.
• Remind your employees to never leave sensitive data documents unattended in the workplace or in public places. Failures in physical security can expose sensitive company data to identity theft, with potentially serious consequences.
All can occur due to physical security breaches, such as the loss of a laptop, the theft of a mobile phone, or the misplacement of a flash drive. As such, they are less likely to result in a data breach if the information on those devices is protected.
Here are some useful examples
Require complex passwords: Require long, complex and unique passwords. And make sure these passwords are stored securely. Consider using a password manager.
Use multi-factor authentication: Require multi-factor authentication to access areas of your network with sensitive information. This requires additional steps beyond logging in with a password, such as a temporary code on a smartphone.

Limit login attempts: Limit the number of incorrect login attempts allowed to unlock devices. This will help protect against intruders.
Encrypt: Encrypt portable devices, including laptops and thumb drives, that contain sensitive information. Encrypt any sensitive data you send outside the company, such as to an accountant or lawyer.

In the case of the user/employee using personal devices to access the company's systems, or for personal use, certain security measures should be taken regarding the use of email, as it can also be a gateway for criminal actions. In the event that employees must use their personal devices to access company systems, employees should report this information to management for logging purposes.

To ensure the protection of company systems, all employees should:

Protecting email systems is a high priority, as emails can lead to data theft, scams and carry malicious software such as worms and bugs. Therefore, users/employees are advised to:

Also known as electronic fraud. Knowing a little more about the most common and dangerous frauds will help us to avoid falling into them. Through these methods, 'phishing' and 'smishing', the attacker seeks to obtain private information such as passwords or credit cards. In this attack, the victim is asked for vulnerable data, such as passwords or access codes, by email, pretending to be the legitimate website or entity, so that the victim provides the data requested by the attacker.

This threat is similar to phishing, the only difference is that it is sent via SMS to phones. The hacker sends a message to our phones, opening the message is not dangerous. The danger lies in clicking on the link, that is when the attack begins.

Most common cyber risks to be aware of. The basic guide of Cybersecurity.
Most common cyber risks to be aware of.

After familiarizing ourselves with the concepts mentioned above, let's take a look at the most frequent risks faced by SMEs, according to studies based on the European Union Cybersecurity Agency (ENISA) survey, with phishing and web-based attacks topping the list.

This type of attack has become extremely popular due to remote working. One careless click on a link is all it takes for a cybercriminal to gain access to sensitive business information.

Cybercriminals will use almost any vulnerability - within an operating system (OS) or application - to carry out an attack. However, most cybercriminals develop web threats that deliberately target some of the most common operating systems and applications.

Many SMEs underestimate the possibility of cyber-attacks due to their size. However, this is precisely what hackers are looking for, as they can quickly profit from a ransomware threat to less secure SMEs.

This type of threat refers to the existence of persons within an organization (whether internal employees or external suppliers, among others) who through carelessness, ignorance and/or bad faith, perform an "action" that affects the security of processes, systems or facilities of an industrial operating environment or critical infrastructure.

The aim of these attacks is to disrupt a company's website so that it is inaccessible, which is done for various reasons by the cybercriminal. A stopped website can lead to loss of revenue, data breaches, customer distrust, and paralysis of the company's activity.
The basic guide of Cybersecurity
1. Determine your vulnerabilities
The first thing to do is to identify your vulnerabilities, so that you know which data to protect. Ask yourself questions such as: ¿What is the most important data that my company stores? ¿Where do you store this data? Once you have the answers, you can start assessing the risks.

2. Protect your devices
Work devices are crucial to the performance of your business. Their internet connection makes them vulnerable to cyber-attacks. Here are some tips to protect them:
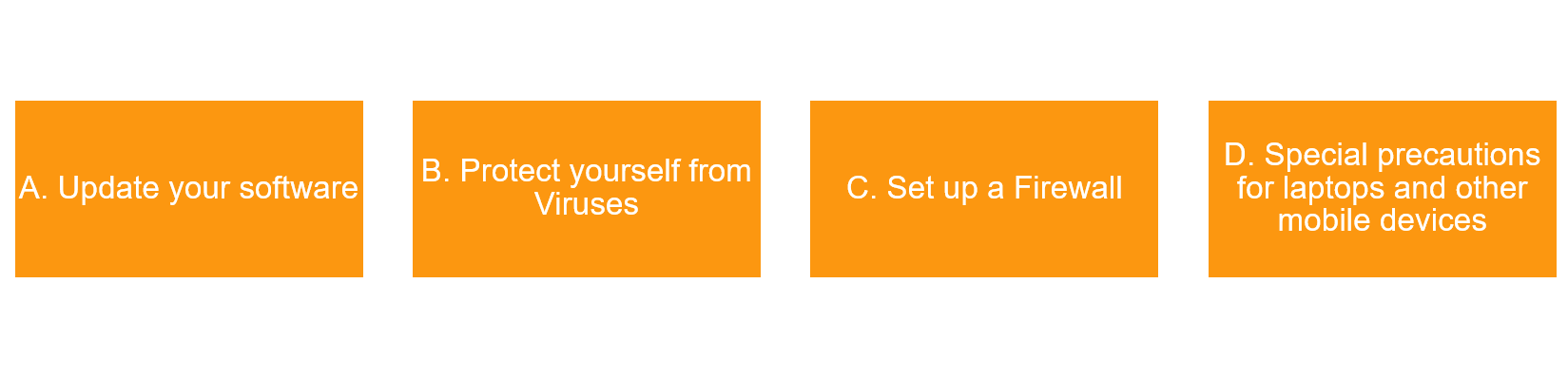
3. Protect your data
No matter what type of business you are in, data is an essential part of it. Data can be damaged in a thousand different ways, one of which is through cyber-attacks. Here are some useful tips on how to protect your data.
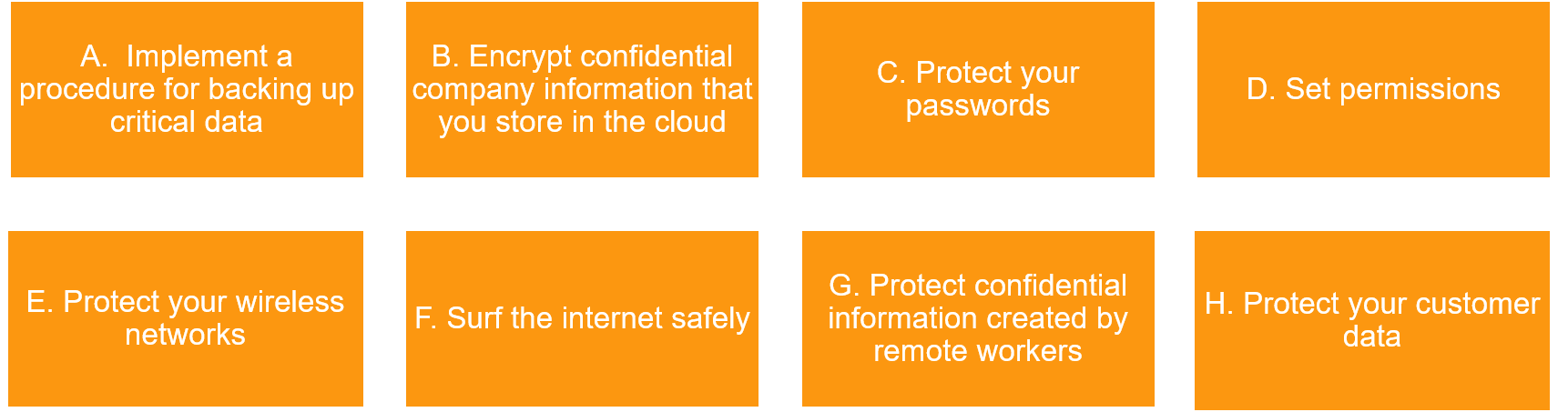
4. Instill cybersecurity in the workplace
The security measures mentioned in this basic guide can help you to significantly reduce the risk of a cyber-attack. But this will be of no use if your company's employees do not have the necessary awareness and training to be able to contribute to the prevention of them. Include this type of training in your company, and don't forget to create a company cybersecurity policy that all team members can follow.

|


 Demo
Demo Play Audio
Play Audio